With more than 500,000 routers in homes and small offices worldwide hacked with malware that can spy on, attack and destroy devices, according to software giant Cisco, the FBI is urging everyone to reboot their routers, pinning the malware on Russia.
In a public service announcement Friday, the FBI said that “foreign cyber actors” are targeting home and office routers and networked devices worldwide using “VPNFilter” malware that can engage in “information collection, device exploitation and blocking network traffic”.
And the defense against the electronic dark arts here, says the agency, is to reboot—immediately and temporarily disabling the malware and helping the FBI to identify the infected devices.
The malware is attacking consumer-grade routers manufactured by Linksys, MikroTik, Netgear and TP-Link, as well as on network-attached storage devices by QNAP.
While the attacks have been building in strength since 2016, the sudden urgency comes as the number of infected devices has abruptly increased over the past three weeks, affecting 54 countries. The attack has intensified to the point that Cisco’s Talos cyber intelligence unit released its warning report, based on months of monitoring efforts, earlier than scheduled and prior to the conclusion of its full investigation.
“We assess with high confidence that this malware is used to create an expansive, hard-to-attribute infrastructure that can be used to serve multiple operational needs of the threat actor,” Cisco researcher William Largent wrote. “Since the affected devices are legitimately owned by businesses or individuals, malicious activity conducted from infected devices could be mistakenly attributed to those who were actually victims of the actor. The capabilities built into the various stages and plugins of the malware are extremely versatile and would enable the actor to take advantage of devices in multiple ways.”
But the FBI’s reboot call only works if the malware is still in stage one. Once it gets to stage two, according to Talos, a reboot won’t help. Phase 2 is where the malware becomes a spy with “workhorse intelligence-collection” capabilities including file collection, command execution, data exfiltration and device management.
By stage three, these capabilities are further boosted, including two plugin modules that are enabled for collecting traffic that passes through the device and theft of website credentials, among other things. Since Talos hasn’t completed its research yet, the depth of the malware’s potential isn’t even known.
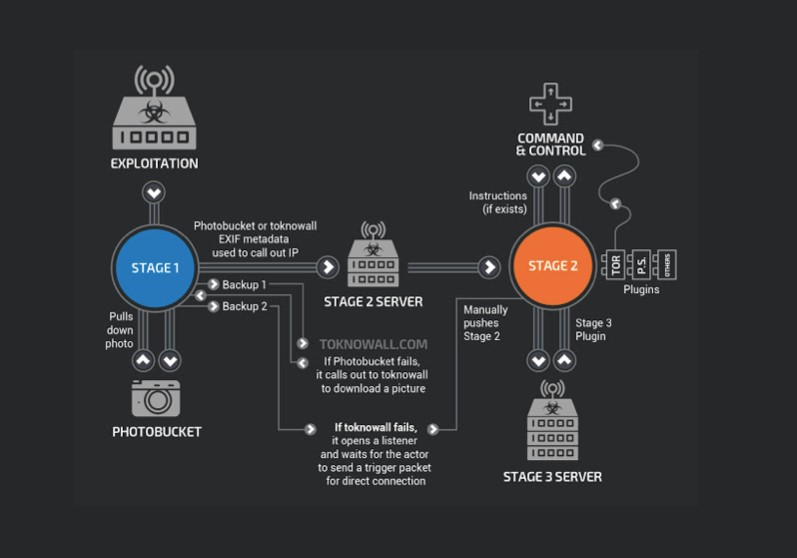
(Click to enlarge)
Cisco is confident that the attack is being controlled by the Russian government based on forensic study of hacking software share codes with malware used in earlier attacks attributed to Russia, though the Kremlin has repeatedly denied any involvement. Related: Does The Turkish Lira Need A New Leader?
"With a network like this you could do anything," Cisco researcher Craig Williams told Reuters.
On Wednesday, a federal judge in Pennsylvania gave the FBI permission to seize an internet domain linked to the Russian hacking group, ‘Sofacy’, which was allegedly being used to control the devices, according to Reuters.
But the ultimate target of the hack is likely Ukraine, says Cisco.
"In particular, the code of this malware overlaps with versions of the BlackEnergy malware — which was responsible for multiple large-scale attacks that targeted devices in Ukraine," Talos said.
Earlier, Russia was blamed for major malware attacks that disabled part of Ukraine’s energy grid and forced factories to close down.
While there are no signs that the malware attack is affecting share prices for the router giants in question, much is at stake beyond information theft apparently originating from Russia.
The global wireless router market is expected to reach over $16 billion by 2025, up from $8.5 billion just last year fueled by massive demand for mobility.
By Jan Bauer for Safehaven.com
More Top Reads From Safehaven.com