For all you know, you’re mining crypto right now—even though you have no idea how to do it, or in some cases, what that even entails.
Thanks to the expansion of cryptocurrencies and the increasing proliferation of blockchain technology, the playing field for hackers has been significantly inflated, with “cryptojacking”—a malware trick that allows hackers to use your devices to mine crypto without your knowledge--hitting outrageous proportions.
Ransomware stole the cyberattack show last year, this year, it’s already a fading trend that is rapidly being replaced by cryptojacking.
While ransomware infects and blocks access to devices or files and holds them hostage for a ransom, sometimes in cryptocurrency, cryptojacking embeds mining scripts on devices without their consent or knowledge, sucking up battery power and compromising performance. In other words, they’re using you to mine crypto, and they’re getting a free ride.
According to a McAfee Labs Threat Report from June, cyberjacking increased by a whopping 629 percent in the first quarter 2018, compared to the last quarter of 2017. Put another way, McAfee registered 2.9 million cryptojacking samples in Q1 2018, compared to only 400,000 in Q4 2017.
Of those mounting cyberattacks, crypto miners make up a huge portion.
According to an investigation in June by cybersecurity firm Kaspersky Lab, incidents of cryptojacking have increased 44.5 percent from the past year. In the same period, the total number of users encountering ransomware fell by nearly 30 percent.
“We have found that ransomware is rapidly vanishing and that cryptocurrency is starting to take its place,” Kaspersky’s report states. Related: American Money Is Moving Abroad
Ransomware might be offer cybercriminals juicier one-off rewards by attacking bigger targets with bigger money, says Kaspersky, but miners take fewer risks with their “sustainable/longer-term model”—even if they are making less money out of their victims.
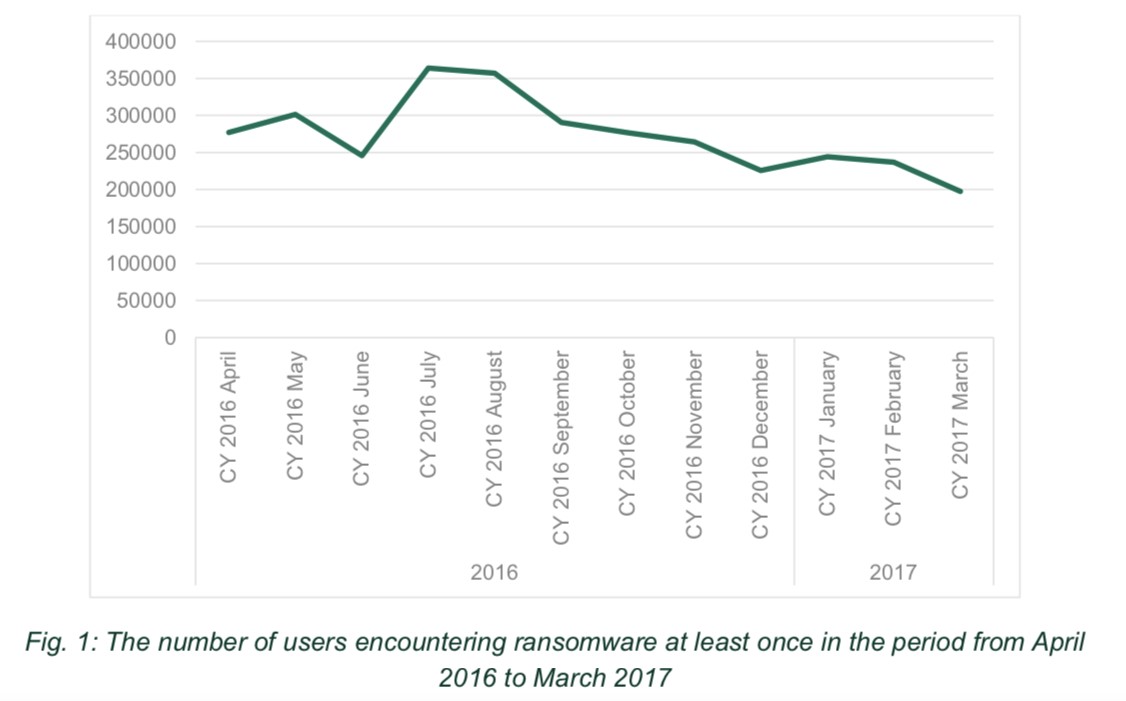
(Click to enlarge)
Source: Kaspersky
McAfee agrees: Cryptojacking is much easier and less risky.
“The goal of the perpetrators is to monetize their criminal activity by expending the least amount of effort, using the fewest middlemen, and executing their crimes in the shortest time possible and with the least risk of discovery,” McAfee says.
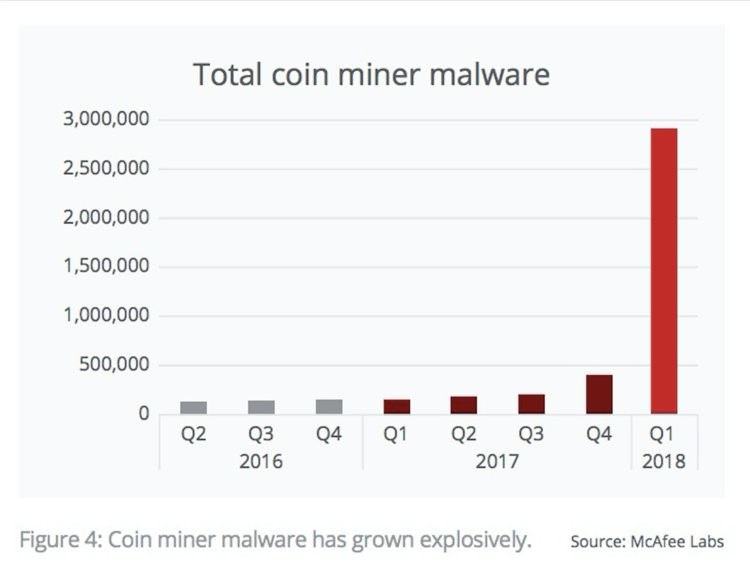
(Click to enlarge)
In June, the GuardiCore security team discovered a malicious traffic manipulation and cryptocurrency mining campaign that had infected over 40,000 machines across various industries, including finance, education, and government.
Japan was also in the spotlight in June when prosecutors arrested 16 individuals suspected of involvement in cryptojacking.
Related: Trade War Reports Send Markets Spinning
Earlier this year, a Russian nuclear facility was also compromised by its own staff who were allegedly mining cryptocurrency using one of the country’s most powerful supercomputers.
Tesla saw its cloud system was hijacked and used to mine cryptocurrency, as well.
But for the casual user, Google and Apple are trying to fight back. As it turned out, even Google’s DoubleClick Ad service was being used to illegally distribute mining software to users—including government websites--without their knowledge.
Google is now updating crypto policy by banning cryptocurrency mining apps. In April, it banned mining apps on its Chrome Store, and in late July it did the same with its Play Store.
Google’s ban does not apply to all software that deals with digital mining, though. Like Apple, it will still allow people to make apps letting them manage mining being done elsewhere, such as cloud computer platforms.
“Apps may facilitate virtual currency storage, provided they are offered by developers enrolled as an organization. In addition, apps may not mine directly for cryptocurrencies, unless the mining is performed in the cloud or otherwise off-device,” according to Apple’s guidelines.
By Damir Kaletovic for Safehaven.com
More Top Reads From Safehaven.com